Harden App Service
Nerdio Manager consists of a number of PaaS services. The entry point into the Nerdio Manager application is the App Service. By default, the Nerdio Manager App Service is protected with Entra ID authentication, including MFA and conditional access, and is accessible from any internet location. It is possible to further protect the Nerdio Manager App Service by using access restrictions or enabling a private endpoint.
Note: Azure App Services also have FTP services enabled by default. These can be fully disabled for Nerdio Manager.
Requirements
To use VNet integration, in some instances, the App Service plan must be Standard, Premium, PremiumV2, or PremiumV3. Please note that some Basic plans support VNet integration. For details, see:
-
Enhanced network security features for App Service Basic SKU
-
Upgrade the Azure App Service
Configure access restrictions on the Nerdio Manager App Service
To configure access restrictions:
-
In the Azure portal, go to App Services and select the Nerdio Manager App Service resource.
Note: It typically has a name in the following format: nmw-app-xxxxxxxxx.
-
In the left menu, navigate to the Settings > Networking.
Note: By default, the configuration is to allow all access.
-
In the Inbound Traffic section, select Access restriction.
-
Select +Add.
-
Type the Name and Description of the new rule.
-
Ensure that Action is set to Allow.
-
Specify the source IP address block to allow access.
Note: This automatically adds a new Deny All rule to the list to prevent access from all other locations.
-
Select Add rule.
-
Once all rules have been applied, navigate to App Services > [your Nerdio Manager App Service name] > Settings > Networking > Public Network Access Restrictions.
-
Under Site access and rules, on the Advanced tool site tab, select the Use main site rules option.
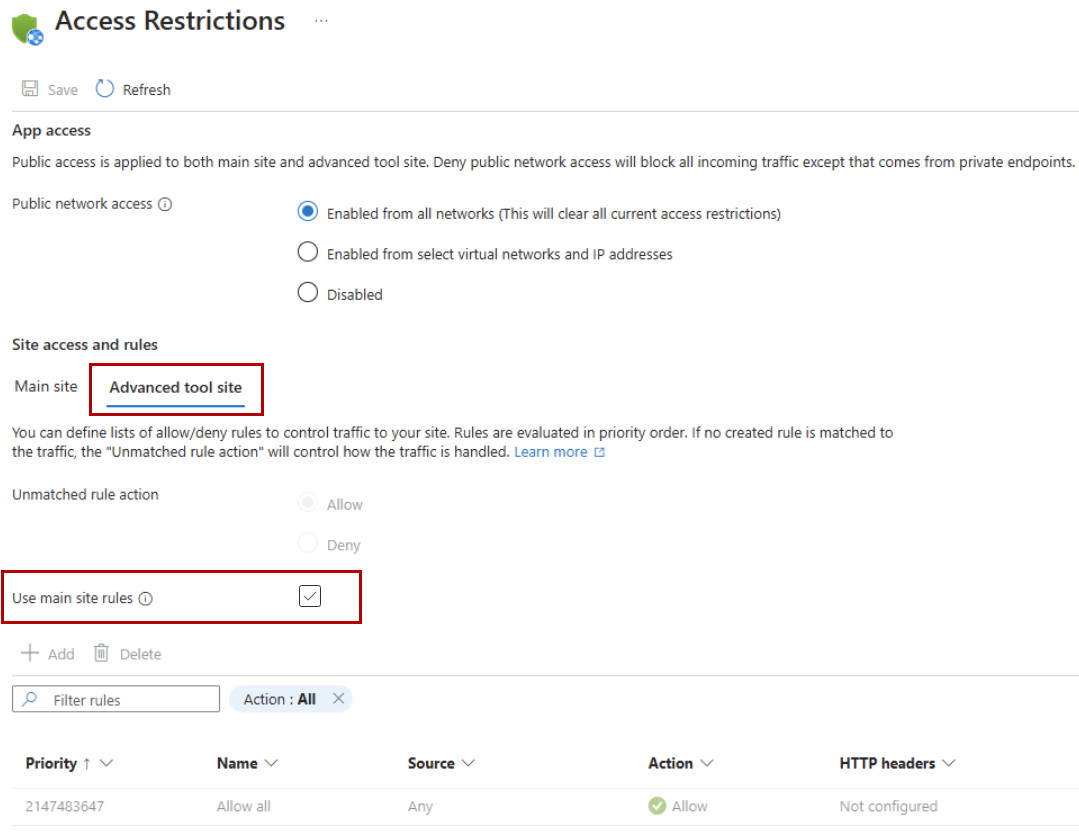
After a few minutes, only allowed IP ranges are able to connect to the Nerdio Manager application.
Create a private endpoint on the Nerdio Manager App Service
-
In the Azure portal, select the Nerdio Manager App Service resource.
Note: It typically has a name in the following format: nmw-app-xxxxxxxxx.
-
In the left menu, navigate to Settings > Networking.
-
In the Inbound Traffic section, select Add.
-
Type a custom Name for the private endpoint.
-
Choose the Subscription containing your VNet.
-
Select the VNet and Subnet where the private endpoint should be attached.
-
Optionally, depending on your VNet DNS configuration, you may be able to select the option for Integrate with private DNS zone.
Notes:
-
Most customers specify custom DNS servers targeting their internal AD environment, in which case this option may be disabled.
-
If Integrate with private DNS zone is not enabled, make sure that the DNS is properly configured to resolve your private endpoint. See Azure Private Endpoint DNS Configuration for details.
-
-
Select OK to save the private endpoint.
After a few minutes, any connections to Nerdio Manager's app service routing to the public IP addresses is rejected. Only connections that resolve your Nerdio Manager URL to the private endpoint IP address succeed.
Disable FTP services on the Nerdio Manager App Service
-
In the Azure portal, select the Nerdio Manager App Service resource.
Note: It typically has a name in the following format: nmw-app-xxxxxxxxx.
-
In the left menu, navigate to Settings > Configuration.
-
Navigate to the General settings tab.
-
On the FTP state selector, change the option from All allowed (default) to Disabled.
-
Select Save.
FTP services are now disabled for Nerdio Manager's App Service.
See also:
-
Harden key vault